Okay, it getting more and more hot 🙂 .
Know we know the fundamental concept’s but how to use it in the real world?
If you and I have a customer, which wants a WiFi network for the engineering- and the marketing-division, which both have their own VLANs, we have several way’s to get this job done, but only one way the make this great. Sure, we could install two autonomous APs, each for one SSID – sounds as bad as is. The question is: How to get AP sending out two SSIDs which each connection to different VLANs in the network?
Trunking or 802.1q is the technique we need. Everyone who is familiar with networking should know this but I can give a short breakout:
VLANs aka virtual LAN’s is the way to virtually split up a network switch.
Why do we need this? In a company with many departments there are many regulations, for example that the network for the engineering and the sales guys is separated from each other. To do this in an oooooooold fashion, we buy two switches, one for the engineering and one for the sales guys. This is connected with a lot of trouble, for example you know must buy and mange two devices.
VLANs allow to do this separation within the switch. Imagine a small 8-port switch, we can configure port 1-4 for the engineering and 5-8 for the lovely sales guys.
So back to topic, back to 801.1q. Now our fantasy company rents’s the second floor in the building, a new switch for this is purchased and our sales- and eng-guys are now distributed on two floors and connected to. But how should sales guy1 send data to sales guy2 if they are each on different floors? Okay, first we need to connect the switches. But as we configured the VLANs, how should the switch on floor2 know to which ports , the traffic received, should forwarded to?
The solution is simple and there a many mnemonic’s to get this in mind, this is my:
On the ports we connect switch1 and switch2 must be configured to do 801.1q tagging. This tagging ensures that the receiving switch know for which VLAN the packet was intended to. It’s like a little pricetag attached to every packet leaving a trunk-port.

So back from out excursion to VLANs…:
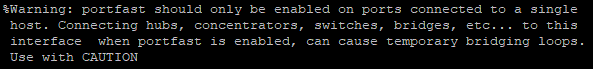
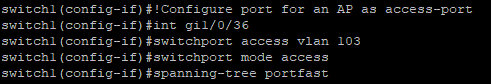
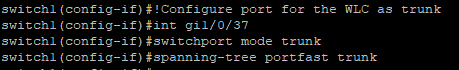
To get two SSIDs, each serving a different VLAN, out of one AP we need MBSSID (multiple base service set identifier). Because our APs are connected via a CAPWAP with the WLC and they don’t need to process the wireless traffic, because this data is send to the AP via the CAPWAP data stream, we configure the ports on the switch for the APs as access-ports. This means this port is only member of one VLAN. This could be a special VLAN where we want to put our APs in or maybe the same as our WLC resides in, the only important thing to keep in mind, the APs must reach the WLC. As the WLC forwards the packets to the different VLANs, it needs the one who get’s a trunk-port. The spanning-tree portfast option uses the newer version of the SPT-protocol and avoid the 30sec delay when connect devices. The last screenshot shows the warning of SPT-portfast, which is normal.
Also you can set the switch to trust DSCP-markings. These markings are used for Quality of Service (QoS). For example voice-traffic from a wireless phone. It’s only useful if these markings are used within your network.
In fact, you will connect the following to static access-ports:
– Lightweight-Access-Points
And this to trunk-ports:
– WLC
– Autonomous APs
– H-REAP APs
H-REAP???
Hybrid-Remote-Edge-Access-Point, is a sub-form of an AP that is processing the data-traffic itself, but farther get’s managed by the WLC with all it’s benefits.
But why I should use H-REAP?
It’s mostly used if your customers owns several branch offices which also needs WiFi.
For this you can centrally deploy a WLC in the headquarter and connect the APs in the branch offices to it. The goal of this design is that the traffic doesn’t flow through the WLC and this will no affect the WAN-link between HQ and the branch, because the APs processing the traffic itself.