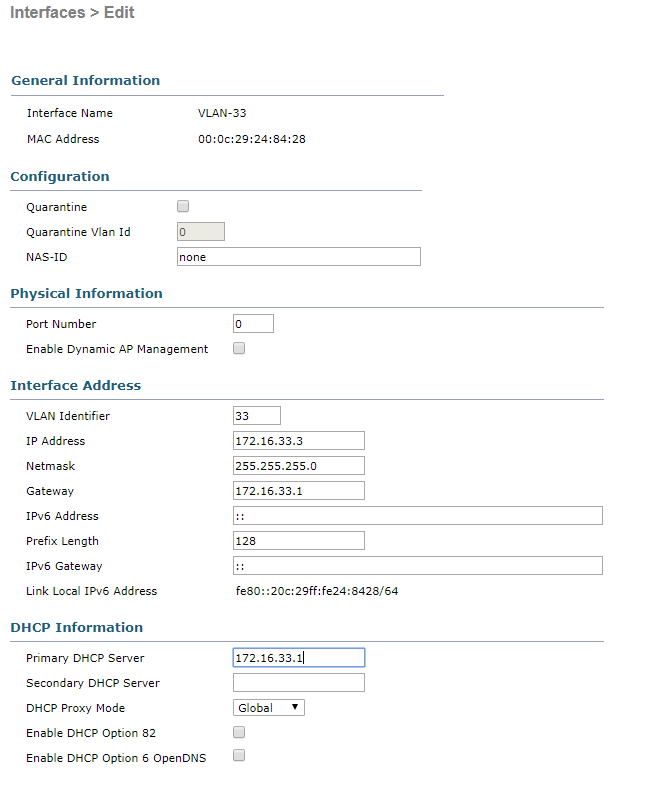
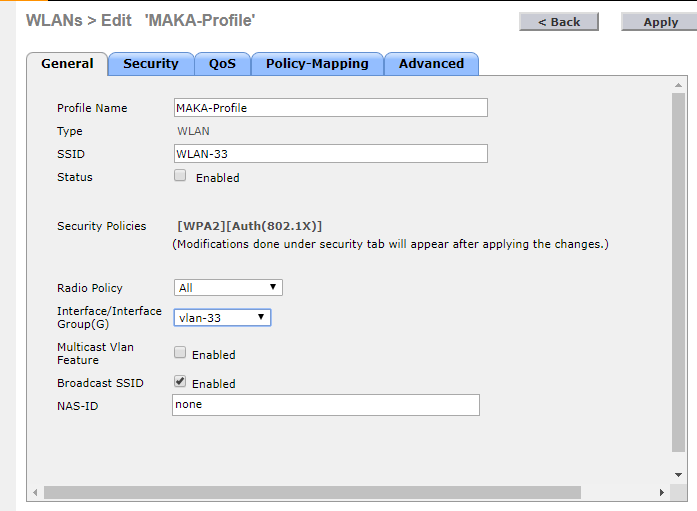
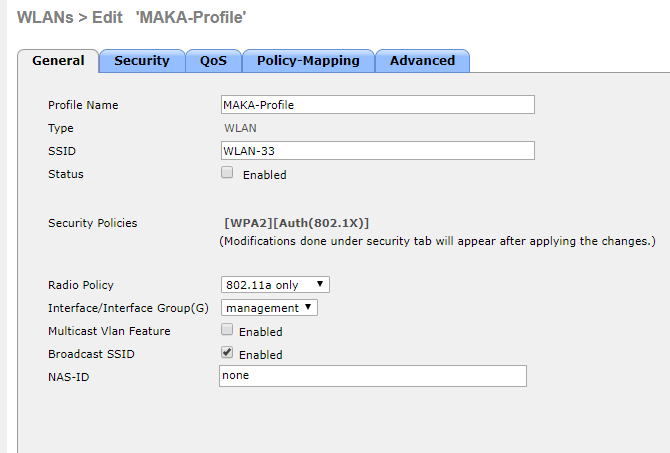
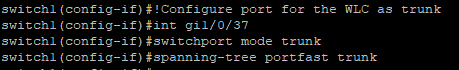
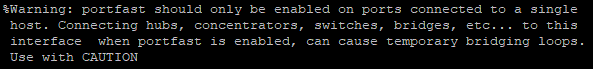
Kommen wir nun zum Thema Sicherheit und zu Technologien die wir auch in Unternehmensnetzwerken einsetzen können.
Die entspannte Basis von 802.1x ist das die Standard Antwort immer NEIN ist.
Recht einfach oder? Aber was wenn nun sich doch mal ein Unternehmens-Laptop mit dem WLAN verbinden möchte? Fangen wir etwas weiter vorne an.
801.1x ist ähnlich eines WLCs eine Verlagerung von Intelligenz. Statt das ein PSK auf einem Access-Point oder einem WLC hinterlegt wird spielt hier ein zentraler Server die wichtige Rolle. Der AAA-Server, Authentication, Authorization and Accounting, sorgt an zentraler Stelle, wie der WLC für die WLAN-Infrastruktur, dafür das Benutzeranmeldungen geprüft und ggf. positiv bestätigt werden.
Jeder Teilnehmer in diesem Prozess bekommt eine Rolle, unser Laptop ist der Supplicant, der Access-Point ist der Authenticator und der AAA-Server nimmt die Rolle des Authentication-Server ein.
In meinen einfachen Worten gesagt: Client will ins WLAN, AP sagt „Erst sagst du mir wer du bist, ich brauche deinen Benutzernamen und dein Passwort“.
Darauf der Client „Okay, mein Benutzername ist „Boss“ und mein Passwort „IRule!“.
Der AP, aka der WLC da wir unsere APs ja als Lightweight betreiben, schickt diese Daten an den für das WLAN hinterlegten AAA-Server und warte dessen Antwort ab.
Dieses ist simpel: JA oder NEIN. Der AAA-Server schaut inzwischen in seiner Datenbank ob der diese Kombination von Username und Password kennt und ob diese berechtigt ist am WLAN teilzunehmen.
Anschließend erhält der WLC z. B. das „JA“ vom AAA-Server und lässt den Client am WLAN teilnehmen. Cool oder?
Als AAA-Server gibt es von Cisco z. B. den ACS oder die ISE, Identity-Service-Engine,
es gibt aber auch viele freie Versionen. Die „Sprache“ die benutzt wird um diese Anmeldung am WLAN durchzuführen ist RADIUS.
Das Framework, also welche Methoden der Anmeldung es gibt sind im EAP, Extensible Authentication Protocol, geregelt. Es gibt hier vier wichtige EAP Varainten:
– LEAP = Lightweight EAP
Einfache Variante wobei sich Supplicant und AAA gegenseitig validieren damit der Client seine Daten nicht einen Bösewicht statt dem AAA sendet.
– FAST = Flexible Authentication via Secure Tunneling
Hier wird ein Tunnel zwischen dem supplicant und dem AAA aufgebaut und die Daten mittels PAC, Protected Access Credentials, versendet. Es benötigt keine digitalen Zertifikate.
– PEAP = Protected EAP
Der AAA-Server präsentiert dem Client sein Zertifikat, der Client prüft dessen Gültigkeit und Authentifiziert sich selbst durch Username und Password.
– EAP-TLS = EAP Transport-Layer-Security
Ähnlich PEAP nur das hier auch der Client ein Zertifikat vorweisen muss damit sich beide Systeme gegenseitig vertrauen.
Wie funktioniert das mit den Zertifikaten?
Platt gesagt, recht einfach. Unser Personalausweis ist sin solches Zertifikat.
Dieser wurde von einer vertrauensvollen Stelle ausgefertigt und unterschrieben, bei dieser kann man jederzeit die Gültigkeit z. B. anfragen. Mit diesem Dokument können wir uns z. B. gegenüber der Polizei authentifizieren.
In der digitalen Welt funktioniert das ähnlich, es gibt diverse öffentliche CAs, Certificate Authorities, oder auch PKI, Public Key Infrastructure, die für z. B. eine Bank, die Online-Banking anbieten möchte, ausstellt. Verbinden wir uns via HTTPS mit unserer Bank sollte das in ungefähr so aussehen:
Unser Browser vertraut dem Zertifikat und stuft die Webseite als sicher ein.
Dies hat er getan in dem er die im Zertifikat enthaltene Signatur geprüft hat, quasi die Unterschrift des Ausstellers des Zertifikats. Damit die Verbindung nun auch wirklich sicher ist soll die Kommunikation verschlüsselt werden, dieses geschieht mithilfe eines Public-Keys den jeder erhält der die Internetseite öffnet. Nun kann unser Browser Daten mithilfe dieses Keys verschlüsseln und nur die Gegenseite, also hier die Bank, hat den sogenannten Private-Key, der es erlaubt die Daten wieder zu entschlüsseln.
???Damit die Sache rund wird, schickt auch unser Browser einen Public-Key an die Bank so das die Kommunikation in beide Richtungen verschlüsselt und damit sicher ist.????
Wir selbst authentifizieren uns meist per User/Password an so einer Webseite.